Information Security
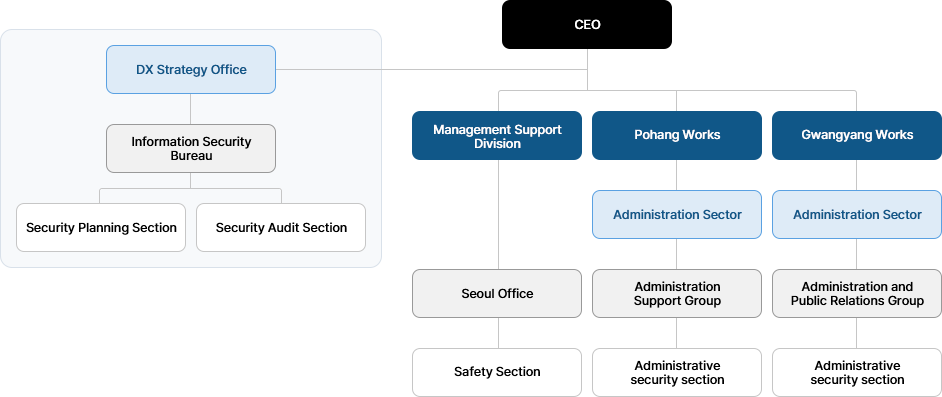
Organization
Information Security Committee
POSCO operates an Information Security Committee that oversees the company’s information security strategies and policies, reflecting both changes in the internal and external security environment and the specific characteristics of our business. The committee reviews and approves company-wide information security policies, which are then embedded into internal regulations and operational processes and implemented across the organization. Through this system, we aim to establish preventive measures against security threats, build a prompt and systematic incident response framework, and ensure business continuity by safeguarding information assets.
- Role : Review the direction and action plans for company-wide information security initiatives and review the formulation, revision, and repeal of information security regulations and guidelines
Operational Status
Security Operations
POSCO operates an integrated information security system that addresses administrative, technical, physical, and human dimensions in response to evolving laws and regulations, technological advancements, and the increasing complexity of the business environment. We continuously monitor and analyze domestic and international information security laws, regulations, and global compliance standards to proactively respond to a broad spectrum of security risks.
Since obtaining ISO/IEC 27001 certification—the international standard for information security management systems—in 2021, we have maintained a globally recognized security framework through regular follow-up audits. In 2025, we further enhanced global customer confidence in our supply chain by obtaining TISAX certification, the information security standard of the European Network of Automotive Exchanges (ENX).
We also provide tailored information security consulting to domestic and overseas subsidiaries, and suppliers, aiming to enhance security capabilities across the entire value chain. Through these efforts, POSCO is committed to three core values: minimizing security risks, ensuring legal and regulatory compliance, and safeguarding the reliability and safety of information assets.
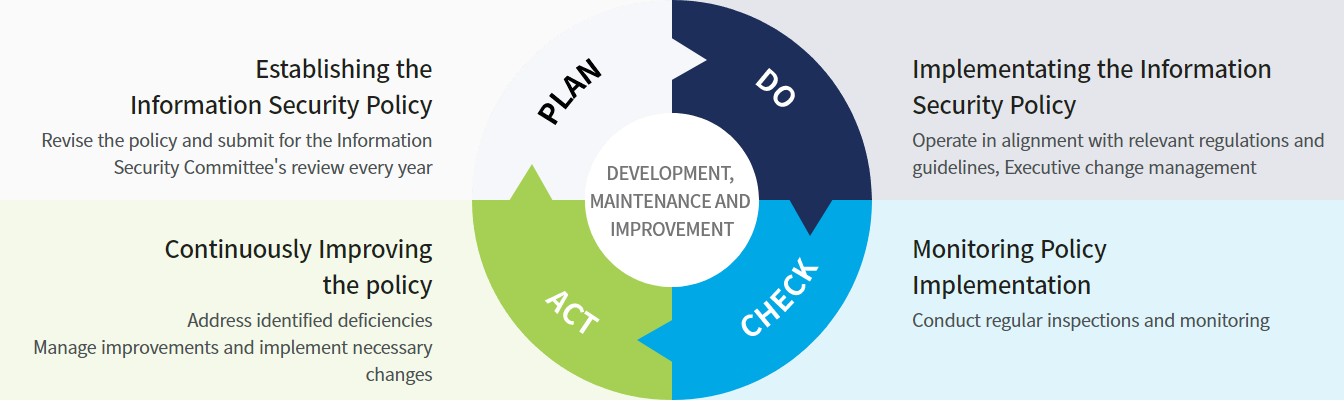
Information Security Policy
POSCO has established Information Security Regulations and Personal Information Security Regulations based on its core Information Security Principles and operates detailed guidelines for specific areas—such as the Document Management Guidelines and Drawing Management Guidelines—to continuously enhance the organization’s overall level of information security. Through this framework, we minimize the risk of security incidents and ensure the protection and stable management of critical information assets.
In particular, we have implemented security management standards that govern the full lifecycle of key information—including documents, drawings, and technical data—ensuring systematic control over storage, transfer, sharing, and disposal. We have also defined and enforced both administrative and technical safeguards to protect the personal information of customers and employees, as outlined in our Personal Information Protection Regulation.
To keep pace with the evolving information security landscape, we update all relevant regulations and guidelines annually in line with the latest laws, systems, and industry standards. These documents are made accessible to employees via the standard document management system, and major updates are communicated through the internal portal (EP), enabling employees to accurately understand and apply the changes.
Core Technologies Protection
Information Protection Across the Steel Value Chain
Information Security Support Activities
- Assess overall security posture and system operation frameworks
- Inspect security system status and support mock hacking simulations
- Strengthen security management capabilities and cultivate security professionals
Risk Management
Cybersecurity Incidents Prevention
POSCO monitors global cyber threat trends in real time through the Group Integrated Security Control Center, which operates 24/7. The Center detects, blocks, and mitigates threats through integration with various security solutions and control systems. It is also building a proactive response system by collecting and analyzing domestic and international hacking attempts and abnormal activities.
To further enhance our defense against external cyberattacks, we conduct security risk assessments during the planning, design, and operational phases of our systems. In addition, we perform regular penetration testing on critical websites and business systems to identify and remediate potential vulnerabilities.
Threat Detection Process
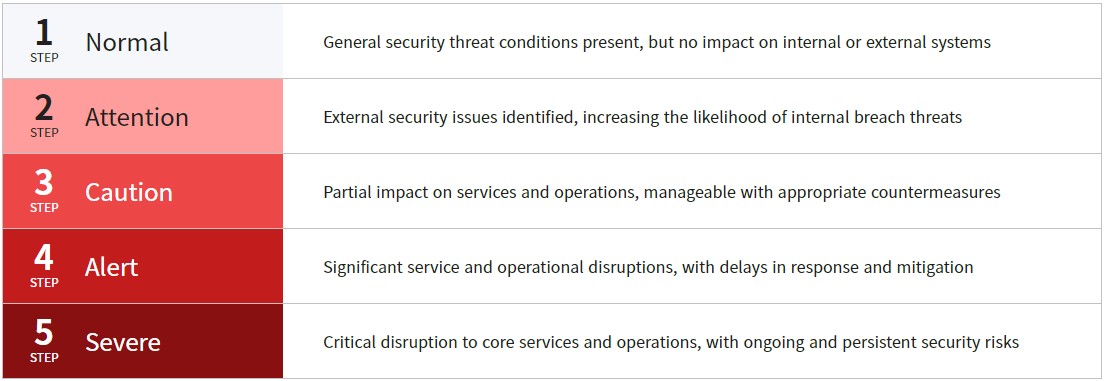
POSCO has established a five-level breach alert system aligned with the National Cyber Crisis Warning Standards set by the Korea Internet & Security Agency (KISA). Based on this framework, we have developed a Cyber Crisis Response Manual that clearly defines response procedures and the roles and responsibilities of relevant departments for each alert level. This system enables immediate and coordinated responses to cybersecurity incidents, helping to prevent the escalation of damage.
POSCO Internal Threat Alert Levels
Metrics and Targets
Security Awareness
Employee e-Learning Results
| Year | Enrolled Partipants | Completed Participants | Percentage |
|---|---|---|---|
| 2020 | 17,982 | 17,909 | 99.6 |
| 2021 | 17,594 | 17,589 | 99.9 |
| 2022 | 17,199 | 17,180 | 99.9 |
2023 | 17,073 | 17,073 | 100 |
2024 | 17,260 | 17,260 | 100 |